Audit
Services focused on determining the level of security in the IT systems of our customers, in accordance with the applicable regulations on both organizational and product domains.
IT Security Audit
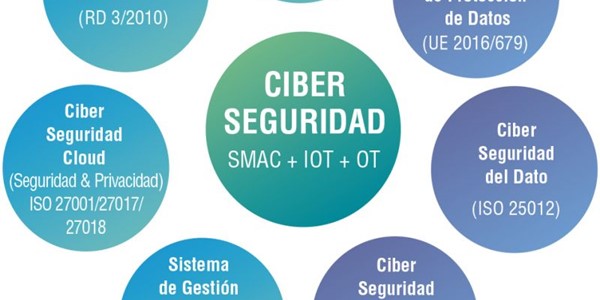
The information systems (IT) security audit includes the analysis and management of systems to identify, enumerate and describe the vulnerabilities detected in the platforms and networks. This analysis is carried out based on a reference methodology (ITIL, COBIT) and complying with the various sections of the ISO27001 Standard.
- Government Model
Organization and Strategy
Analysis and Evaluation
Politics and procedures - Management and Control
Enumeración de Redes, Topología, S.O. and protocols
Vulnerability Detection in Services and Applications
Specific Correction Measures
Recommendations on the implementation of preventive measures - Audit Reports

SW Security Audit
It consists of the execution of source code audits throughout the SW development life cycle, by security reviews at every development iteration
- Web Security Audit (OWASP)
- Mobile Applications Audit (apps endpoints)
- Source Code Audit (static, dynamic and runtime analysis)
- Fuzzing techniques

Phising
They are simulations of attack via email to a certain number of employees in order to obtain credentials of access to systems or other information, identifying the equipment, connection, user or any other data of the person who executed it, all agreed with the client. It also includes the use of 'fake' files stored in USB sticks and dispersed voluntarily to measure the level of awareness of people in cybersecurity.
Ethical hacking & Pentesting
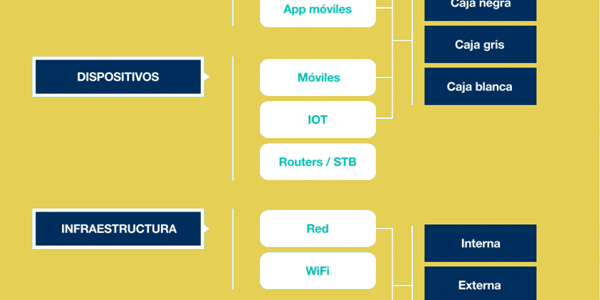
Ethical Hacking or IT Security Audit consists of attacking under controlled conditions the IT security system of an organization in order to detect potential vulnerabilities. There are different types and approaches to ethical hacking. DEFSEC uses internationally recognized security review methodologies, such as OSSTMM, NIST SP 800-115, OWISAM and uses the CVVS standard for the assessment of vulnerabilities and risks, as well as the CWE standard for identifying public vulnerabilities
- Perimeter Analysis (Pentesting from the outside)
- Internal Analysis (Pentesting from the inside)
- Wifi network analysis (OWISAM)
- Cloud Analysis
















